Services
Integration Services
Connect your security, identity, apps, and ITSM—so signals become actions.
Why EEMC for Integrations
Outcome-driven automations, zero-trust alignment, and maintainable interfaces.
Outcome-Driven Automations
From alerts to automated actions with measurable MTTR gains.
Zero-Trust Alignment
Identity-centric patterns, least privilege, and policy enforcement.
Maintainable & Observable
Versioned connectors, logging, tracing, and clear documentation.
What We Integrate
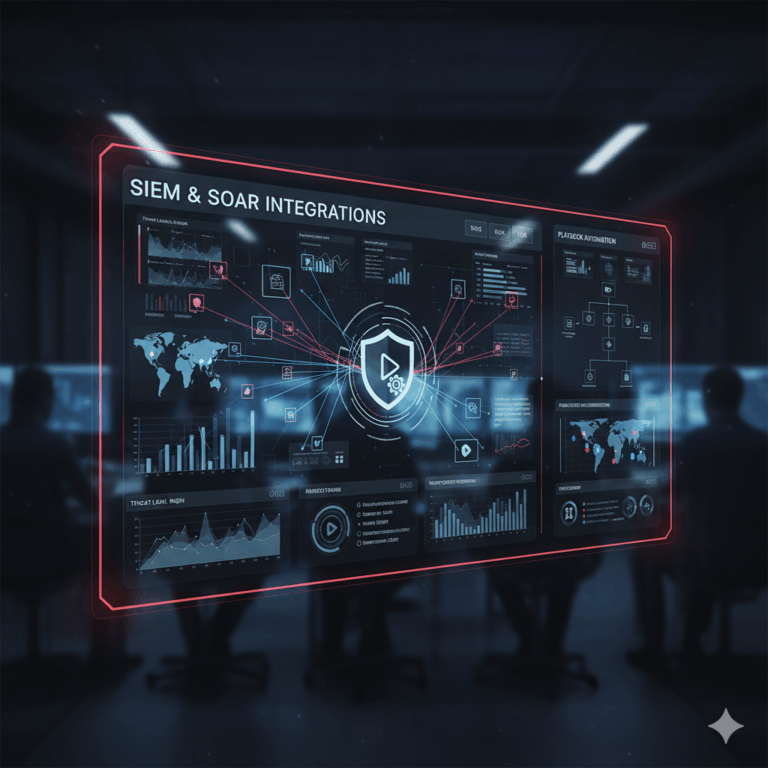
- SIEM & SOAR integrations with third-party tools
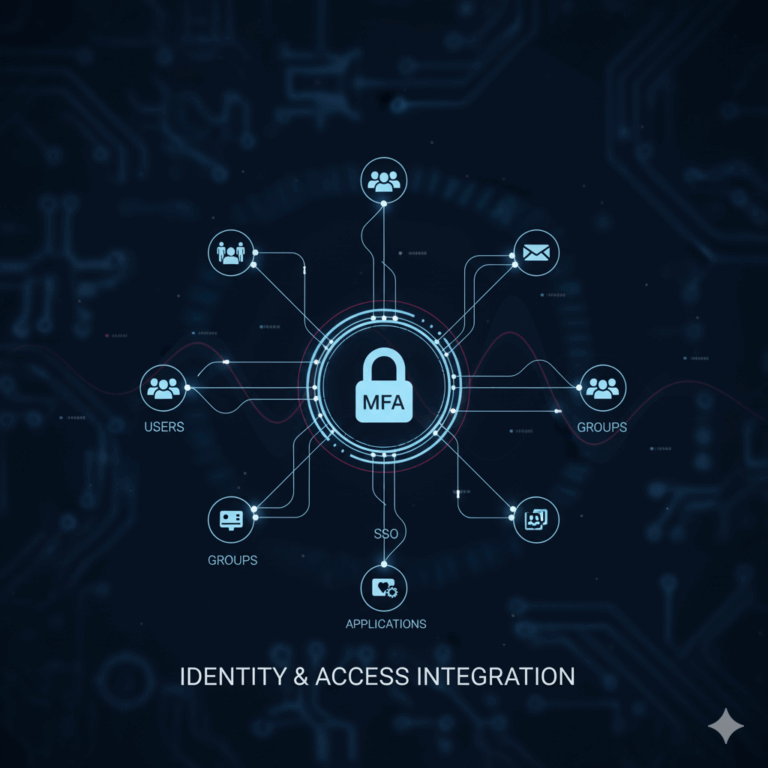
- Identity & Access Management integration
- Secure API integrations between enterprise applications
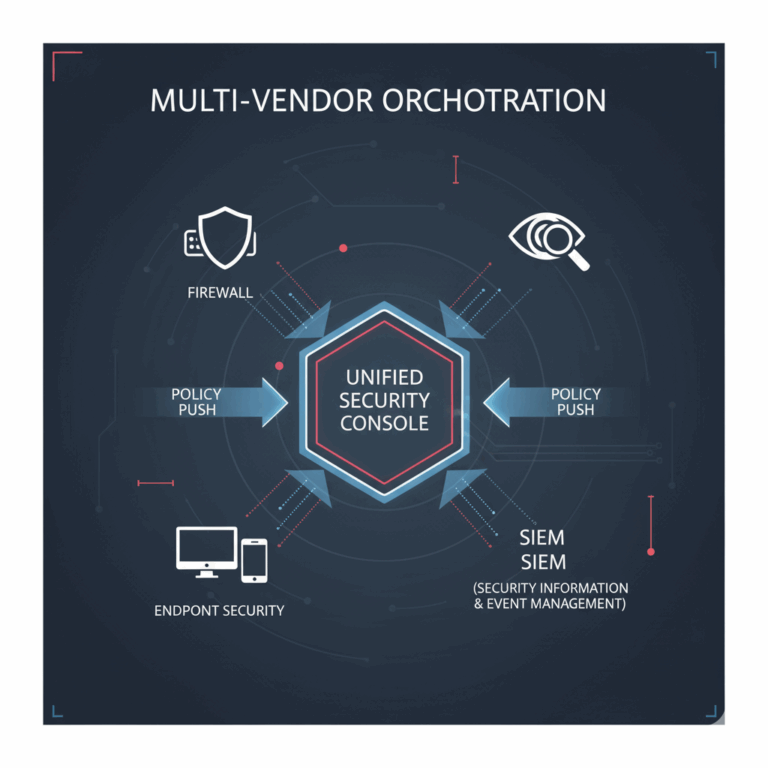
- Multi-vendor system orchestration (firewall + endpoint + SIEM)
- ITSM tool integration
- Centralized print management solutions



Integration Lifecycle
A secure, testable path from idea to production.
- Discover & Map: sources, targets, event models, constraints.
- Design & Secure: schemas, auth, scopes, rate limits, policies.
- Build & Simulate: connectors, playbooks, sandboxes, unit tests.
- Validate & Hardening: UAT, failure modes, idempotency, runbooks.
- Operate & Improve: SLIs/SLOs, dashboards, cost & usage tuning.
Value You Can Measure
99.5%+
system uptime / stability
75–85%
incident reduction rate
70–80%
operational efficiency gain
Integration outcomes vary by environment and architecture; validate per engagement.
FAQ
Yes—vendor-agnostic approach with clear interface contracts.
OAuth2/OIDC, signed webhooks, mTLS, scoped secrets, least privilege policies.
Yes—hybrid patterns with brokers, message buses, and secure tunnels.
Diagrams, code/config repos, secrets process, runbooks, monitoring dashboards.


