Specialized Professional Services
Independent testing and hardening to validate risk—and prove resilience.
Why EEMC for PT/VA & Audits
Methodical testing, clear evidence, and remediation you can action.
Threat-Realistic
Adversary-style techniques mapped to MITRE ATTACK where appropriate.
Evidence-Rich
Screens, payload traces, and reproducible steps—not just scores.
Fix-Focused
Prioritized remediation with configs, references, and retest option.
What We Deliver
- Penetration Testing & Vulnerability Assessments (PT/VA)
- Secure configuration audits (firewalls, servers, endpoints)
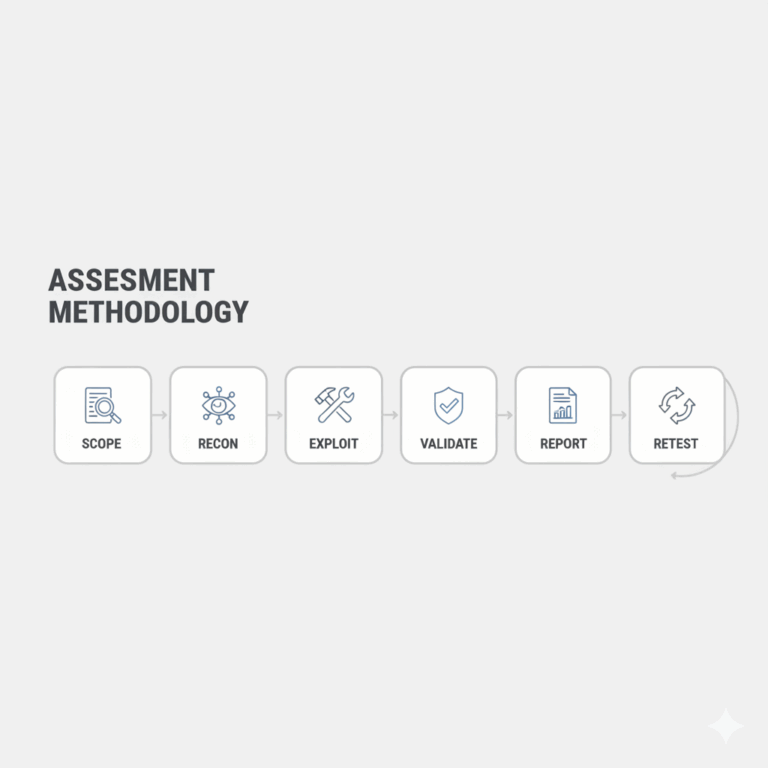
Our Assessment Method
Transparent, repeatable, and aligned to your change windows.
- Scope: goals, in/out of scope, rules of engagement, change freeze dates.
- Recon & Model: enumerate assets, attack surface, threat model.
- Exploit & Validate: safely attempt exploitation, confirm impact, avoid disruption.
- Report & Prioritize: CVSS/likelihood, business impact, remediation plan.
- Retest & Verify: confirm fixes, update residual risk, executive summary.

Deliverables
Everything you need to brief leadership and guide engineers.
Executive Summary
Risk heatmap, key findings, before/after posture, and next steps.
Technical Report
Evidence, PoC details, reproduction steps, and affected assets.
Remediation Plan
Prioritized fixes with configs, references (e.g., CIS), and tracking.
Value You Can Measure
95%+
on-time project delivery
ROI+
positive return on service across projects
<3%
rework rate (Service Quality Index)
FAQ
We coordinate change windows and use safe techniques; high-risk actions are sandboxed or simulated.
Yes—network, web, API, identity, and cloud resources with agreed scopes and ROE.
Yes—our remediation plan includes configs and we offer retesting to verify closure.
We provide signed reports summarizing scope, approach, and outcomes for stakeholders.


